Zoiper Account Set Up
Zoiper for Bizphone System
Download and install: Go to the link and download the right version for your computer platform. https://www.zoiper.com/en/voip-softphone/download/current
Save the downloaded file, then find and run the Zoiper installer in your downloads directory.
Installation: Click Next on the next few steps to accept Zoiper’s default settings.
Open Zoiper Application
The account information should have been provided by Bizphone.
If not please contact Bizphone Support 617 945 8900
Get Started
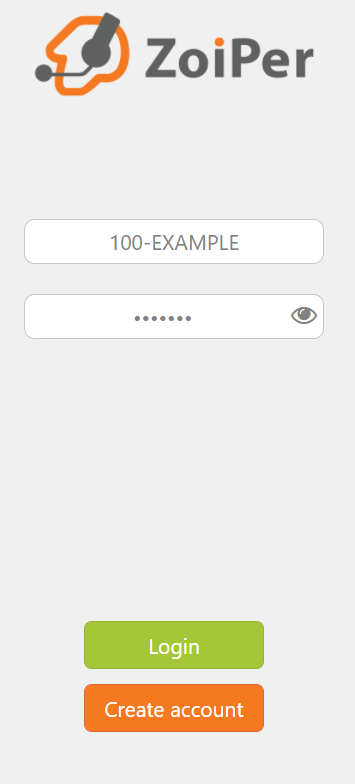
- Enter your Account Extension and Password….example: 100-EXAMPLE then click Login
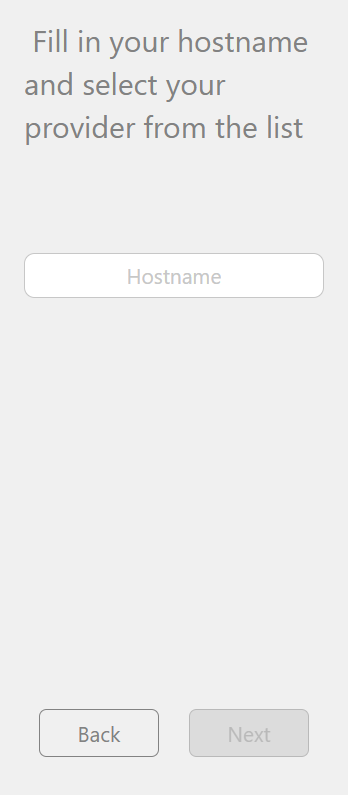
2. Enter Domain/Hostname info then click Next
3. Check Optional and enter Account Number and Domain/Hostname then click next
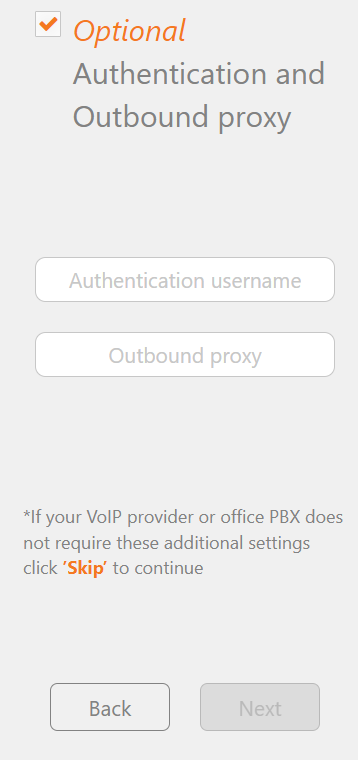
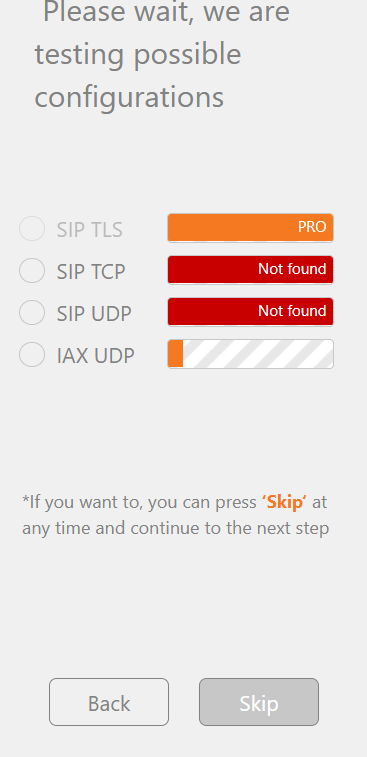
3. Click Skip and Yes to skip on pop up
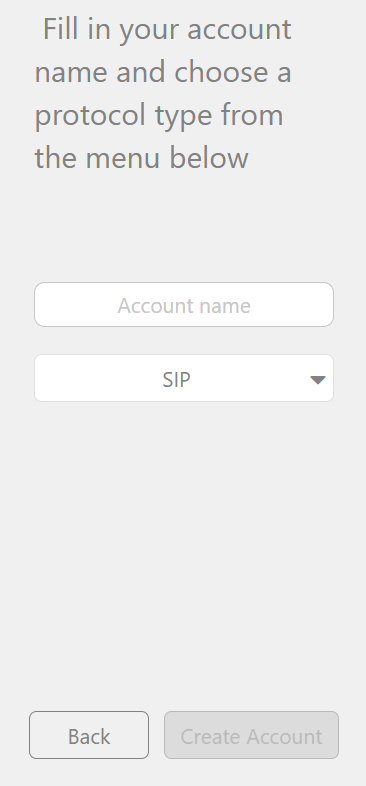
3. Enter Account Extension Number again and click Create Account
Check the account Check Mark status: If green the account successfully registered.
If not GREEN select the account and check the information again.
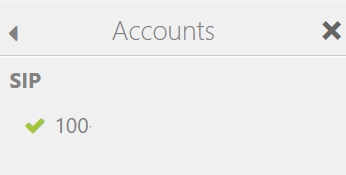
Click the black X to head back to main account screen
Main Screen